Cloud account takeover attacks have evolved beyond simple credential theft. Cybercriminals are now exploiting OAuth applications to maintain persistent access to compromised environments, bypassing traditional security measures like password resets and multifactor authentication.
Cloud account takeover (ATO) attacks have become a significant concern in recent years, with cybercriminals and state-sponsored actors increasingly adopting malicious OAuth applications as a means to gain persistent access within compromised environments.
These attacks allow malicious actors to hijack user accounts, conduct reconnaissance, exfiltrate data, and launch further malicious activities.
Proofpoint researchers have demonstrated how these attacks can be fully automated, and threat actors are already actively exploiting these vulnerabilities in the wild.
The security implications are particularly concerning. Once an attacker gains access to a cloud account, they can create and authorize internal (second-party) applications with custom-defined scopes and permissions.
This capability enables persistent access to critical resources such as mailboxes and files, effectively circumventing traditional security measures like password changes.
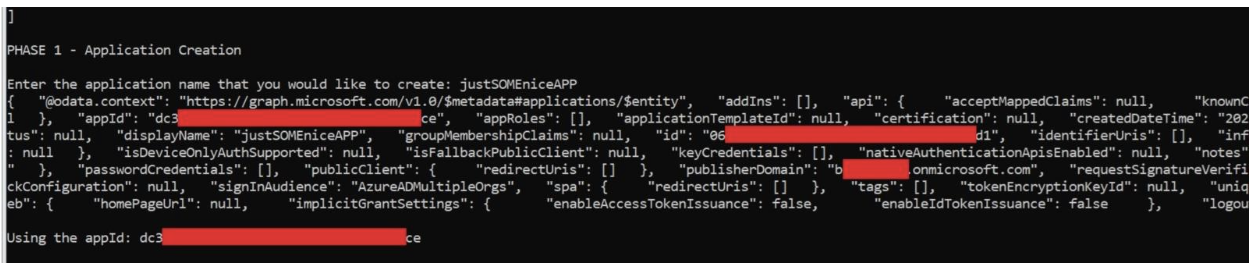
To better understand and demonstrate this attack vector, Proofpoint researchers have developed a tool that automates the creation of malicious internal applications within a compromised cloud environment.
This provides an in-depth technical analysis of that tool and its implications for enterprise security. Additionally, real-world incidents detected through telemetry offer concrete evidence of how threat actors are actively exploiting such vulnerabilities in the wild.
Understanding OAuth Application Types
In the context of cloud environments, particularly Microsoft Entra ID, it’s crucial to understand the distinction between second-party and third-party applications.
Second-party applications are registered directly within an organization’s tenant. Also known as internal applications, they are generally created and managed by the organization’s administrators or users with appropriate privileges.
Second-party applications inherit a level of implicit trust within the environment, as they originate from within the organization’s own directory.
Third-party applications are registered in external tenants and request access to resources in other organizations’ tenants. Common examples include widely-used services like Zoom or DocuSign.

Third-party applications typically undergo additional scrutiny through administrative consent workflows and organizational security policies before being granted access.
This distinction is particularly relevant from a security perspective, as threat actors often prefer creating second-party applications during post-exploitation phases.
These internal applications can be more difficult to detect and may bypass security controls designed primarily for external application monitoring.
How Attackers Establish Persistent Access
Cybercriminals often leverage a combination of techniques to gain initial access to cloud user accounts. One common tactic is the use of reverse proxy toolkits accompanied by individualized phishing lures that enable the theft of credentials and session cookies.
Once the attackers have stolen a user’s login credentials, they can establish unauthorized access to the targeted accounts, setting the stage for the next phases of the attack.
This visibility in standard administrative interfaces underscores the importance of regular application auditing and monitoring, as malicious applications may blend in with legitimate business applications unless specifically scrutinized.


Following successful initial access, attackers often pivot to creation and deployment of malicious OAuth applications. This process typically involves leveraging the compromised account’s privileges to register new internal applications, configuring specific permissions and API scopes for maximum impact, and authorizing these applications to access critical organizational resources.
The strategic value of this approach lies in its persistence mechanism: even if the compromised user’s credentials are reset or multifactor authentication is enforced, the malicious OAuth applications maintain their authorized access.
This creates a resilient backdoor that can remain undetected within the environment indefinitely, unless specifically identified and remediated.
Proofpoint researchers have developed an automated toolkit which demonstrates methods by which threat actors establish persistent access through malicious OAuth applications.
The proof-of-concept implements several key capabilities that mirror real-world attack scenarios, including automated OAuth application registration and configuration, customizable permission scope selection, persistent access mechanism independent of user credentials, and configurable application naming conventions.
Starting from an initially compromised account, the tool streamlines the post-exploitation process through automated application creation.
While this demonstration uses randomized application names, real-world threat actors typically employ deceptive naming strategies that mimic legitimate business applications to avoid detection.
During the automated deployment process, an application is registered with pre-configured permission scopes that align with the attacker’s objectives.
A critical aspect of this implementation is the ownership attribution: the compromised user account becomes the registered owner of the newly created application, effectively establishing it as a legitimate internal resource within the organization’s environment.
This ownership model provides several tactical advantages. The application appears as an internally developed resource and the authentication requests originate from within the organization’s tenant.
The application inherits trust relationships associated with internal resources, and standard third-party application security controls may not detect or flag this activity.
Upon successful application registration, the tool automatically establishes two critical authentication components: application secret generation and token harvest.
The tool first creates a cryptographic client secret for the application, which serves as the application’s own authentication credential. The automation then proceeds to collect multiple OAuth token types, including an access token, a refresh token, and an ID token.
Following the password reset, the tool demonstrates the sustained effectiveness of the malicious application’s access through several key activities.
It successfully retrieves user mailbox contents and maintains continuous access to incoming and historical emails, now operating independently of user credential changes.
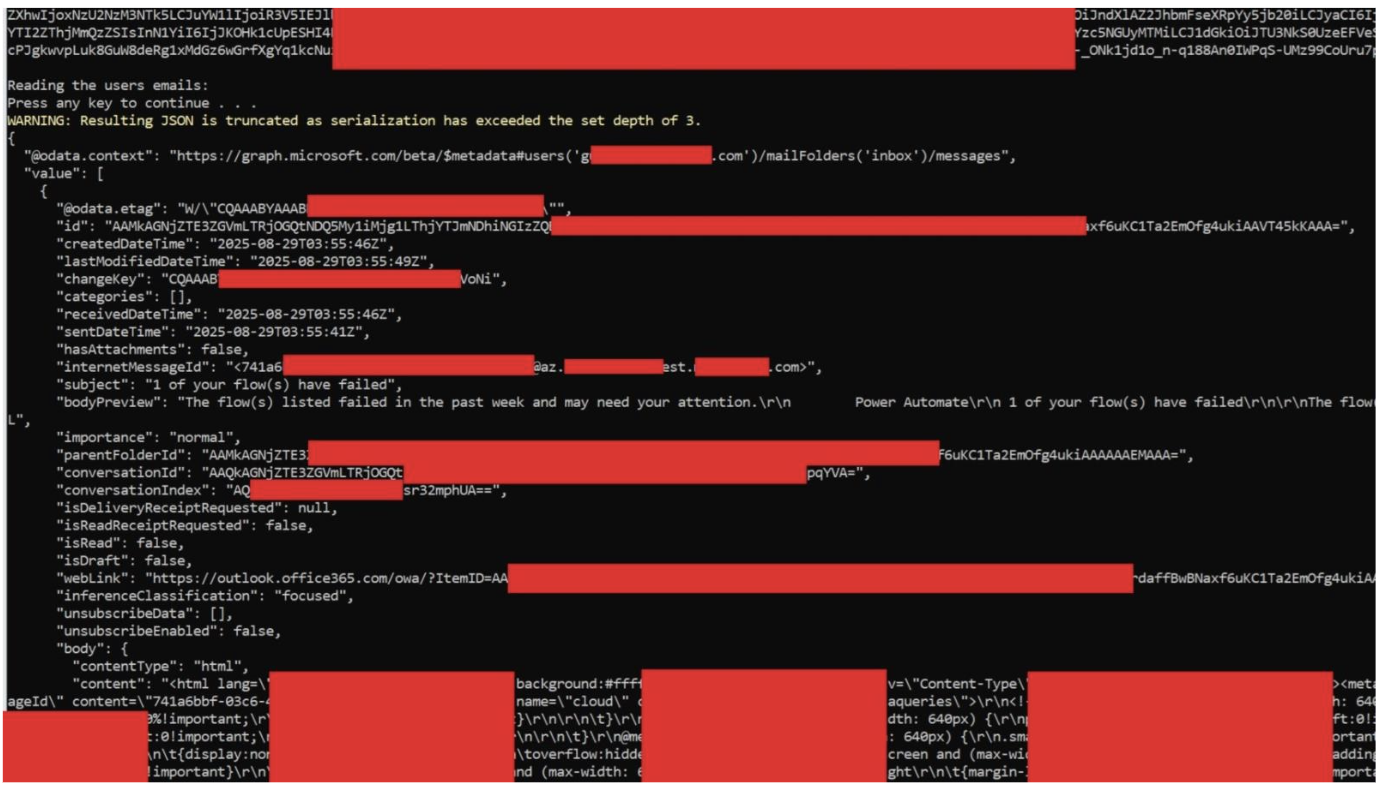

The scope of unauthorized access extends well beyond email, encompassing SharePoint documents, OneDrive stored files, Teams messages, calendar information, organizational contacts, and other Microsoft 365 resources.
Real-World Attack Observed in the Wild
Proofpoint telemetry revealed a real-world account takeover incident that persisted for four days. The initial compromise was detected through a successful login attempt using a user agent signature most likely associated with Adversary-in-the-Middle (AiTM) phishing attacks, specifically the Tycoon phishing kit.
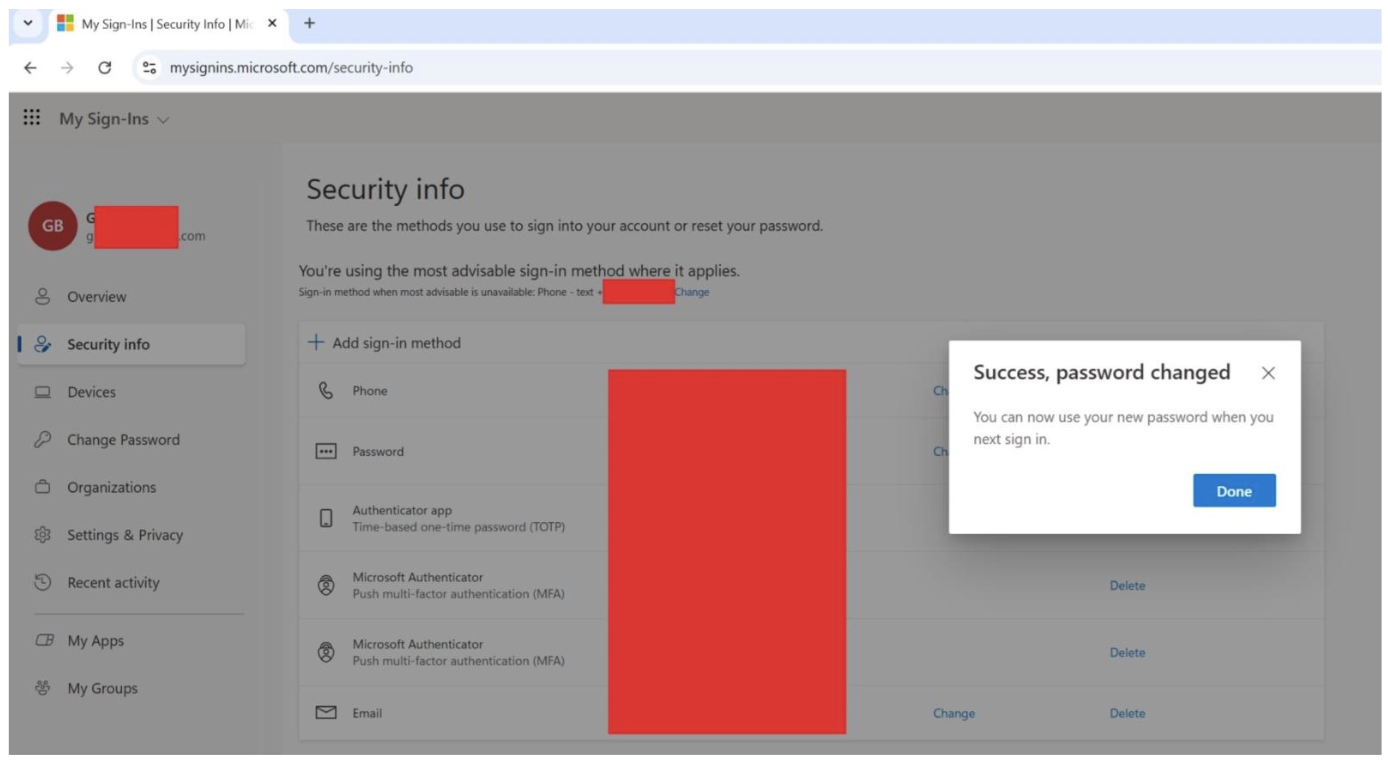

The threat actor, operating through US-based VPN proxies, executed several malicious actions: created malicious mailbox rules, registered an internal application named ‘test’, and added application secrets with Mail.Read and offline_access permissions, enabling persistent access to the victim’s mailbox even after password changes.
After approximately four days, the user’s password was changed, following which failed login attempts were observed from a Nigerian residential IP address, suggesting the threat actor’s possible origin. However, the application remained active.
This case study serves as a concrete example demonstrating that these threats are not merely theoretical, but active, exploited risks in the current threat landscape.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.